Adaptive Authentication
Roaming users and remote access to organizations’ confidential data is becoming a larger security concern leading to a conflict of interest of maintaining usability while increasing security. When users log in with standard credentials, such as a username and password, it makes them vulnerable to cyberattacks. Two factor Authentication (2FA) or multi factor authentication (MFA) are strong solutions that provide better security by requiring additional credentials, but end-users do not always adopt the solutions easily because it can’t adapt to user access scenarios on the fly.
What if there was a solution that not only matched an organization’s policies and compliance standards but provided a dynamic solution that applied context to the authentication process; thus, provides a seamless and easy to use authentication option for all users. This is the definition of Adaptive Authentication (also known as Contextual Authentication) which asks for different credentials, depending on the situation, making it difficult for a hacker to compromise data while still providing an easy user experience for qualified employees.
What is Adaptive Authentication?
Adaptive authentication is a form of two factor authentication that takes into account the context of the end user’s access request. The process starts when the authentication method identifies various parameters about the user, like their location, device, network, application, and time of day. These contextual parameters give access to authorized users while creating major obstacles for unauthorized users. By utilizing this approach, security policies can be configured to the context in which users are logging in down to the group, OU, or even individual. This can then require more or fewer authentication requirements. For example, it can easily require stronger authentication for individuals that are accessing company data outside of the office.
Adaptive authentication not only provides an added level of security but better usability to authorized users, such as users that are working within the company building. This authentication method provides the ability for your company to be compliant, secure, and provide a user-friendly option for your employees. Deploying this authentication method allows you to ” hassle the hackers, not the end users “.
Adaptive authentication is also known as risk based authentication as it measures that risk level based on the context of the authentication request. Based on this risk, users may have to experience an additional authentication request. If a user is requesting access after work hours in a different location, they may need to fulfill an additional authentication factor.
Factors for Adaptive Authentication
Configurations and specifics typically differ for each organization’s risk policy, but here are some of the standard parameters that are considered context about the user’s access scenario:
- IP Address/Network – The IP address of your client is something that cannot be easily spoofed or falsified. Rather than use a “black list” approach where certain blocks of addresses are deemed “bad,” a white list is much more manageable and assigns a positive credibility score to IPs controlled by the organization. The controlled confines of a LAN are a very different environment from an Internet café. The other caveat with this type of information is that proxy servers could be used to mask the IP of the end-user’s actual device. Some vendors can utilize client-side apps to determine what “type” of network connection the device is using. It can detect encryption strengths for Wi-Fi connections and treat those using outdated or weak encryption as a higher risk.
- Geolocation – There are a few ways to get a user’s location. IP-based geolocation is fairly easy to implement but does not have a high degree of accuracy. It may only be reliable to determine which country the user is in! HTML 5 now has built-in support for Geolocation and is supported by all major browsers. When used by “honest” users, this is generally more accurate since it could use a mobile phone’s internal GPS or the wireless access points available around a workstation. Due to privacy concerns, this information is only provided if the user allows it. The specification specifically states that the data may not return the actual location and some browsers even allow you to provide a specific latitude and longitude to requesting servers, so authentication decisions for sensitive applications should not rely on this type of data.
- Device Information – Certain information is available from each HTTP request your web browser makes. The browser vendor and version (aka “User-Agent”) are typically present as are capabilities or supported file types or fonts. Some device “fingerprinting” can be done using this information, but all this data can be completely spoofed. Some client-side apps can integrate directly into your device or browser, allowing it to get authoritative information and securely deliver it to the web server.
- Cookies – This can be considered a subset of the “device information” type but one that is a little more controllable. If the user chooses to “remember” their device, the server can generate an opaque, random identifier and set it as a persistent cookie in the user’s browser. The lifetime of this cookie is typically configurable. The presence or absence of this cookie can be used to establish whether the device has previously been used which can boost credibility. If HTTPS is used to communicate with the authentication server, then the cookie should be relatively safe from replay attacks.
- Time of day – Another factor that cannot be spoofed is the current time. Maybe a defined time window represents a slight increase in credibility. Any access outside this Monday through Friday time is deemed riskier. Historical usage patterns can be established for the user as well to help weight this factor more appropriately.
How does Adaptive Authentication Work?
Adaptive authentication is driven by granular security policies. When you first deploy adaptive authentication for your organization, you outline the login requirements for your users using security policies, which will determine what level of authentication is required based on the parameters of the user’s login request. For example, for a remote employee, the policy can say that when they are at their home address, on their usual IP address, only minimal authentication may be required. Whereas if their location showed as a foreign country outside of their usual working location, you could block the request all together. These controls can be implemented to be stricter based on the user’s role and the level of sensitivity the data has that they are trying to access.
Each security policy can be thought configured for a group of users, OU, or individuals. The security policy is where your user’s known geographical location, device information, IP address, and more are defined. Every time your users request access to the system, their request undergoes a risk-based evaluation, and dependent on this risk score, the user may need to provide additional credentials. Adaptive authentication can also enable a zero trust architecture. If the user is requesting access to highly confidential information or resources, they will need to enter another authentication factor that identifies the user, like biometrics. This further secures the confidential information from insider and outsider threats.
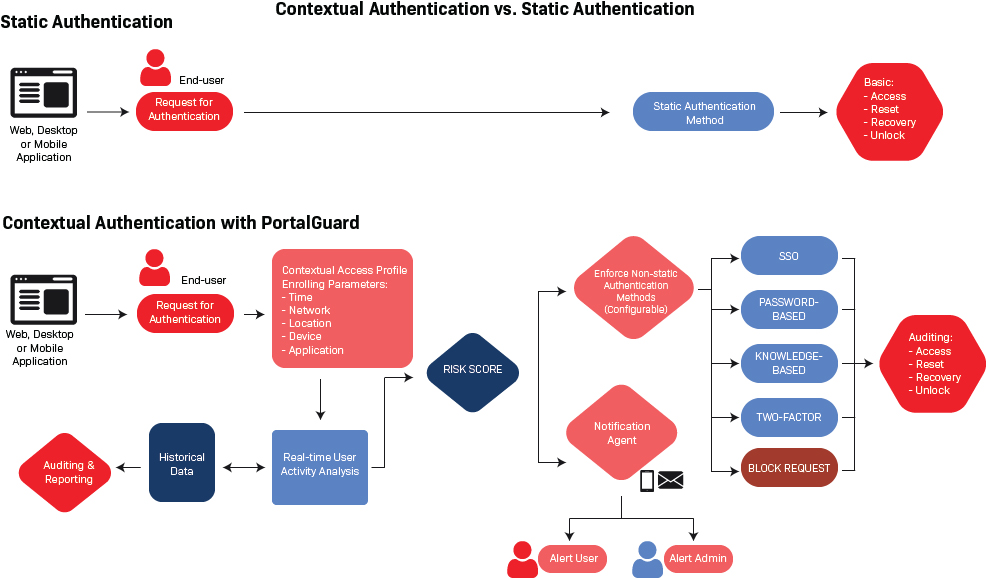
Contextual Authentication vs Static Authentication
As an alternative to static authentication solutions, PortalGuard understands the midpoint and handles the challenges of remote user access scenarios. By taking a cost-effective, flexible approach to authentication, PortalGuard offers five levels of authentication (Single Sign-On, Password-Based, Knowledge-Based, Two-Factor Authentication, and block a request).
Using PortalGuard’s Contextual Authentication, organizations can now gain insight into user access scenarios allowing them to make security and usability adjustments transparently to the user and dynamically adjust the authentication method to what is appropriate based on the user’s situation. Obtaining the user’s contextual data is optional with PortalGuard and all options can be configured down to the individual user, group, or application levels.
Does Adaptive Authentication Prevent User Fraud
With Adaptive Authentication, organizations can prevent user fraud. Since contextual authentication accounts for more than a static username and password, stealing confidential information is more difficult for threat actors. Imagine threat actors trying to break into your account in the middle of the night. While you may not notice, the barrier to entry is significantly harder to break. The security system understands you are typically online during your usual work hours, but not randomly at 3 am. That is when threat actors if attempting to compromise your account, will have to fill out secondary forms of authentication that they will not have access to, such as a hardware token or biometric.
Benefits of Adaptive Authentication
- Increase security without impacting the end-user experience
- Increase usability for authorized users while creating barriers for unauthorized users
- Configurable – to the user, group or application levels
- Lower Total Cost of ownership than token-based Two-Factor Authentication alternatives
- Proactive approach to reducing threats – block suspicious users in real-time before a login attempt is made
See PortalGuard’s Adaptive Authentication in Action
Enjoy this brief demo of PortalGuard’s Adaptive Authentication capabilities then sign up for our free trial to try it out for yourself.