
SAML for Single Sign-On
Today, organizations face the challenge of managing multiple user repositories while also striving to address user complaints regarding password fatigue. To overcome these hurdles, a robust Single Sign-On (SSO) solution is essential. One such solution that has gained widespread adoption and proven effectiveness is Security Assertion Markup Language (SAML). With SAML, organizations can streamline user access and enhance security by leveraging its flexible and powerful features.
For a more detailed overview, check out the SAML for SSO ebook.
What is SAML?
SAML, developed by the OASIS Security Services Technical Committee, is an industry-standard protocol for seamless web browser SSO. It is an XML-based authentication protocol that enables the exchange of identity assertions between SAML-enabled applications. When a user requests access to a resource, an online Identity Provider (IdP) creates a SAML token containing the user’s identity assertions. The resource server then validates the SAML request, granting the user access without the need for additional passwords.
Why choose SAML for Single Sign-On?
SAML offers several compelling reasons for organizations to adopt it as their SSO solution:
- Compatibility: SAML works seamlessly with both cloud-based and on-premise services. It is independent of operating systems (such as Windows, Mac, and Linux) and device architectures (PCs, iPads, smartphones), making it universally accessible.
- Network-friendly: SAML utilizes HTTP/HTTPS protocols, which are commonly open in server or client firewalls. This feature simplifies network administration and ensures smooth communication between client devices and servers.
- Centralized authentication: SAML enables organizations to redirect user authentication to a single Identity Provider. This centralized approach allows for easier implementation and enforcement of network and access policies.
- Versatility: SAML supports authentication against any user repository using various authentication methods. This flexibility ensures compatibility with existing systems and provides a seamless user experience.
Benefits of SAML for Single Sign-On
SAML, as one of the most widely used SSO protocols, offers numerous benefits and simplifies application integration for supporting applications. Some of the advantages of implementing SAML SSO include:
- Reduced Password Burden: SAML SSO reduces the number of passwords users have to remember and manage, enhancing convenience and security.
- Enhanced User Credential Management: SAML SSO eliminates the requirement to manage external user credentials, simplifying administration processes.
- Stronger Authentication: SAML SSO supports authentication methods like Multi-factor Authentication or Adaptive Authentication, enabling organizations to enforce stronger security measures for specific users or groups (e.g., Administrators).
- Decreased IT Support Calls: Implementing SAML SSO reduces password-related support calls and access issues, leading to improved efficiency and cost savings. Despite misconceptions surrounding SAML SSO, such as concerns about implementation time and cost, organizations can actually reduce expenses and optimize time. Research from Forrester estimates that a single password reset through the help desk costs an organization approximately $70, while Gartner suggests that 20% to 50% of helpdesk calls are related to password resets. Considering these figures, implementing SAML Single Sign On becomes a compelling choice.
- Controlling System and Network Segment Access: One of the key features offered by an SSO Identity Provider is access control, which allows organizations to control and manage access to different system and network segments. By integrating with a preferred directory, the Identity Provider utilizes Access Control Lists (ACL) and other defining characteristics to granularly restrict access to resources at the Organizational Unit level. The most advanced Identity Providers offer extensive customization options, enabling organizations to establish highly detailed access policies.
- Enforcing Least Privilege: SAML plays a crucial role in implementing and enforcing the Principle of Least Privilege (POLP). POLP dictates that users, processes, and programs should be granted the minimal access rights necessary for their intended functionality. With SAML, organizations can effectively manage and control access to resources, ensuring that users are granted only the precise permissions required for their tasks. By integrating SAML into their access control framework, organizations can enhance system stability and security while reducing the risk of unauthorized access and potential data breaches.
- Minimizing Exposed System Targets: One of the key advantages of SAML for SSO is its ability to consolidate individual login points into a single, secure access point. While this consolidation may raise concerns among users who worry that reducing login routes could compromise security, a well-configured SSO solution enhances both security and usability. By implementing SSO through a dedicated Identity Provider, all other access points are effectively closed, leaving only one entry point. This consolidation significantly reduces the attack surface, mitigating potential vulnerabilities. Proper SSO configuration ensures that security measures can be maximized without sacrificing usability, providing a seamless and secure SSO login experience for end-users.
How does SAML Single Sign-On work?
The following steps demonstrate how a SAML Identity Provider, such as PortalGuard, functions using two different SSO methods: SP-Initiated (Service Provider) and IdP-Initiated (Identity Provider).
SP-Initiated Single Sign-On
SP-Initiated SSO occurs when a user attempts to log in directly to the desired service without first authenticating to the local Identity Provider. If the user has not yet authenticated, they are required to log in using local credentials, which are sufficient to grant access to the requested service. The steps for achieving this are outlined below.
STEP 1: The user opens the browser on the client machine and accesses the target server; e.g. https://mail.google.com/a/example.com
STEP 2: The target server sees that the user has not yet authenticated, it generates a SAML request and returns it alongside the originally requested URL (the “RelayState”) to the client machine as hidden input fields in an HTML-form response.
STEP 3: JavaScript in the response automatically submits the form to the PortalGuard Identity Provider.
Note: The user can be forced to log in using any of PortalGuard’s SSO authentication methods – including Multi-Factor Authentication, Adaptive Authentication, and Identity-Bound Biometrics.
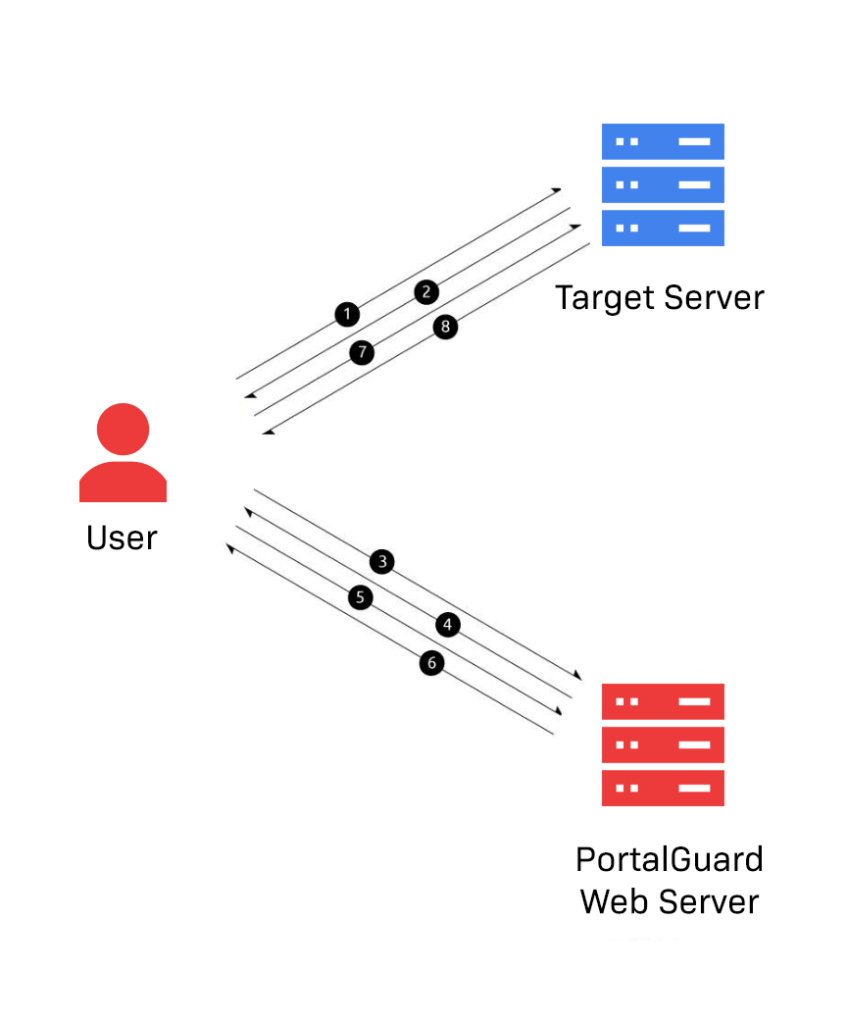
STEP 4: The user is presented with the PortalGuard login screen. The user enters the appropriate username/password and clicks “Login”.
Note: this login screen can be fully customized to match the specific branding of your organization, creating a seamless experience for the user. The user can reset a forgotten password from the login screen.
STEP 5: PortalGuard validates the submitted username and password in real time against the appropriate directory. If correct, the client machine will have established a session with the PortalGuard web server.
STEP 6: The original SAML request is now serviced by the PortalGuard Identity Provider. It generates a SAML response and sends it along with the “RelayState” back to the end user browser, wrapped in an HTML form.
STEP 7: JavaScript in the HTML response automatically submits the form to the target server’s Assertion Consumer Service (ACS). Both the SAML Response and “RelayState” are included in this form data.
STEP 8: The target server parses and validates the SAML response. It uses the embedded identity claims to verify the user identity and then grants the user access to the application.
IdP-Initiated SSO
IdP-Initiated SSO typically occurs when a user accesses a locally managed jump page. By authenticating directly to the Identity Provider first, the user can choose from a host of services to access without the need to input any additional credentials. The technical process for achieving IdP-Initiated SSO is outlined in the steps below.
STEP 1: The user opens the browser on the client machine and accesses the target server; e.g. https:// mail.google.com/a/example. com
STEP 2: The PortalGuard login screen is presented to the user if they do not already have an active session.
STEP 3: The user enters his/her username and password and clicks “Login.”
STEP 4: PortalGuard validates the submitted username and password in real time against the appropriate directory. If correct, the client machine will have established a session with the PortalGuard web server.
STEP 5: The user is granted access to the SAML Identity Provider jump page.
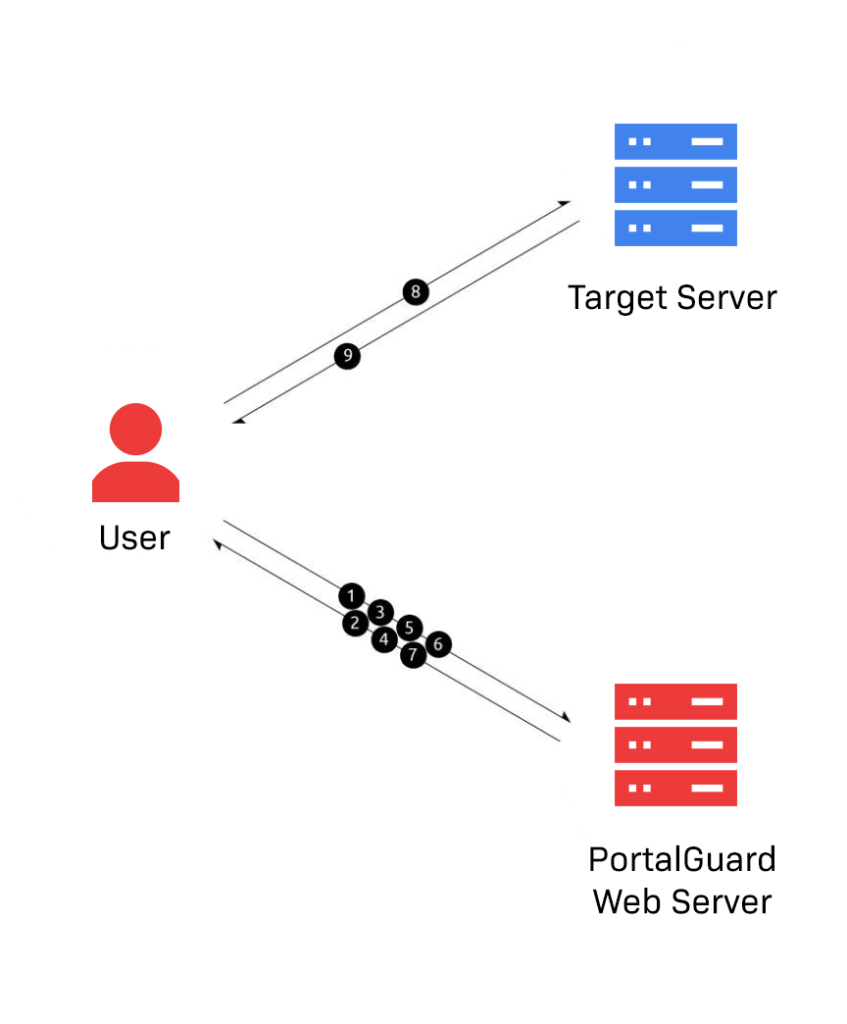
STEP 6: The user clicks a displayed application. Note: the applications available to the user are configurable by the administrator.
STEP 7: The click is serviced by the PortalGuard Identity Provider, which generates a SAML response and sends it back to the end-user wrapped in an HTML form.
STEP 8: JavaScript in the response automatically submits the form to the target server’s Assertion Consumer Service (ACS).
STEP 9: The target server parses and validates the SAML response. It uses the embedded identity claims to determine the user’s identity and grant the user access to the application.
SAML Single Logout
For more information on how SAML Single Logout works, read our blog SAML Single Logout: Simplifying User Session Management.
When do you need SAML SSO?
Determining the need for SAML SSO involves considering various factors and understanding the benefits it can offer in your specific environment. To identify when SAML SSO is necessary, it is important to evaluate the problem areas that exist within your environment. Some of these problem areas may include:
1. Multiple password prompts are impeding access:
- Lost productivity for end-users due to time wasted on logging in or re-logging in when sessions time out.
- Applications used infrequently are more susceptible to forgotten passwords.
2. End-user password fatigue:
- Managing a large number of passwords can lead to frustration.
- Juggling multiple passwords reduces convenience for end-users.
- Using the same passwords for multiple applications compromises password security.
3. IT support or Help Desk handles forgotten password calls:
- Loss in productivity for IT support employees due to the volume of password-related calls.
- Password-related calls can be expensive for enterprises, averaging $70.00 per call1.
- IT support hours and staffing may become challenging, especially for global companies.
SAML SSO Alternatives
While many web applications are compatible with SAML SSO, there are cases where certain applications may not support it. In such situations, alternative solutions can be explored to achieve seamless integration across your organization.
One alternative to consider is form-based single sign-on. With form-based SSO, users authenticate themselves through a web form rather than relying on SAML authentication. This method allows for integration with applications that cannot directly support SAML, enabling a streamlined sign-on experience for users.
Another option to enable SSO for non-SAML applications is Kerberos. Kerberos is a network authentication protocol that uses tickets to authenticate users and enable secure communication. By leveraging Kerberos, organizations can establish single sign-on capabilities for applications that do not natively support SAML.
When considering SAML SSO alternatives, it’s important to assess the specific requirements and capabilities of your applications to determine the most suitable solution for your organization’s needs.
For more information about the different types of SSO protocols visit the Types of Single Sign-on Protocols page.
See PortalGuard’s Single Sign-On in Action
Enjoy this brief demo of PortalGuard’s Single Sign-On capabilities then sign up for our free trial to try it out for yourself.